Client Server Architecture

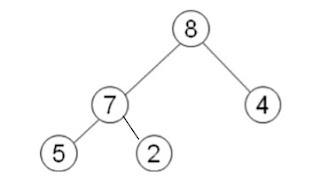
CLIENT SERVER ARCHITECTURE Client/server architecture is a computing model in which the server hosts, delivers and manages most of the resources and services to be consumed by the client. This type of architecture has one or more client computers connected to a central server over a network or internet connection. Client server application consists of multiple application system combines or divided but interlinked to make various layers or tier The application logic tier. The application logic tier is where all the “thinking” happens, and it knows what is allowed by your application and what is possible, and it makes other decisions. This logic tier is also the one that writes and reads data into the data tier. The data tier. The data tier is where all the data used in your application are stored. You can securely store data on this tier, do transaction, and even search through volumes and volumes of data in a matter of seconds. The presentation