Are you a programming enthusiast looking to stay ahead of the curve in 2023? With the ever-evolving tech landscape, keeping up with the Best Programming Language to learn can be a daunting task. Fear not, as we have compiled a list of the top 10 Programming Languages that you should consider learning in 2023. Python: This versatile language continues to dominate in 2023, with its ease of use, readability, and a vast library of modules. JavaScript: As web development grows increasingly popular, JavaScript remains a crucial player, with its ability to create dynamic and interactive web pages. Java: This language has stood the test of time and remains a popular choice for enterprise software development. C++: A staple in the gaming and systems development industries, C++ offers exceptional performance and memory management. Swift: Apple's preferred language for iOS app development, Swift continues to grow in popularity with its simplicity and reliability. R: As data science and machin...
Implementation Of Mono Alphabetic Cipher Encryption-Decryption
- Get link
- X
- Other Apps
Mono Alphabetic Cipher Encryption-Decryption
Introduction
It is Better than Caesar Cipher. If, instead the “cipher” line can be any permutation of the key 26 alphabetic characters, then there are 26! Or greater than 4 * 1026 possible keys. This is 10 orders of magnitude greater than the key space for DES and would seem to as a Mono-alphabetic substitution cipher, because a single cipher alphabet is used per message.
There is however, another line of attack. If one analytically knows the nature of the plain text, then the analyst can exploit the regularities of the language.
Limitations
- Monoalphabetic ciphers are easy to break because they reflect the frequency data of the original alphabet.
- A countermeasure is to provide multiple substitutes, known as homophones, for a single letter
C Progrm to Encryp the imputed text using Mono Alphabetic Cipher.
#include <stdio.h>
#include <string.h>
int main()
{
char pt[52] = {'A', 'B', 'C', 'D', 'E', 'F', 'G', 'H', 'I', 'J', 'K',
'L', 'M', 'N', 'O', 'P', 'Q', 'R', 'S', 'T', 'U', 'V',
'W', 'X', 'Y', 'Z', 'a', 'b', 'c', 'd', 'e', 'f', 'g',
'h', 'i', 'j', 'k', 'l', 'm', 'n', 'o', 'p', 'q', 'r',
's', 't', 'u', 'v', 'w', 'x', 'y', 'z'};
char ct[52] = {'Z', 'Y', 'X', 'W', 'V', 'U', 'T', 'S', 'R', 'Q', 'P', 'O',
'N', 'M', 'L', 'K', 'J', 'I', 'H', 'G', 'F', 'E', 'D', 'C',
'B', 'A', 'z', 'y', 'x', 'w', 'v', 'u', 't', 's', 'r', 'q',
'p', 'o', 'n', 'm', 'l', 'k', 'j', 'i', 'h', 'g', 'f', 'e',
'd', 'c', 'b', 'a'};
char p[20] = {'\0'}, c[20] = {'\0'}, r[20] = {'\0'};
int i, j;
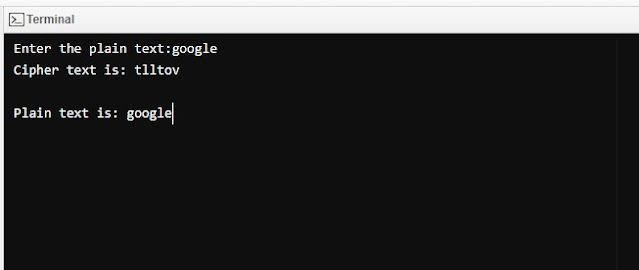
printf("\n Enter the plain text:");
scanf("%s",p);
for (i = 0; i < strlen(p); i++)
{
for (j = 0; j < 52; j++)
{
if (pt[j] == p[i])
{
c[i] = ct[j];
}
}
}
printf("\n Cipher text is: %s", c);
for (i = 0; i < strlen(c); i++)
{
for (j = 0; j < 52; j++)
{
if (ct[j] == c[i])
{
r[i] = pt[j];
}
}
}
printf("\n \nPlain text is: %s", r);
}
- Get link
- X
- Other Apps
Popular posts from this blog
Eliminating Epsilon transition (ε-Transitions) | Conversion of Epsilon-NFA to DFA | Conversion of Epsilon-NFA to NFA | Theory Of Computation (TOC)
Theory Of Computation (TOC) | Eliminating Epsilon Transition ( ε -Transitions) : Given any Epsilon NFA (ε-NFA) , we can find a DFA D that accepts the same language as E. The construction is close to the subset construction, as the states of D are subsets of the states of E. The only difference is that dealing with ε-transitions, which can be done by using ε-closure.
Top 10 Programming Language to learn in 2023
Are you a programming enthusiast looking to stay ahead of the curve in 2023? With the ever-evolving tech landscape, keeping up with the Best Programming Language to learn can be a daunting task. Fear not, as we have compiled a list of the top 10 Programming Languages that you should consider learning in 2023. Python: This versatile language continues to dominate in 2023, with its ease of use, readability, and a vast library of modules. JavaScript: As web development grows increasingly popular, JavaScript remains a crucial player, with its ability to create dynamic and interactive web pages. Java: This language has stood the test of time and remains a popular choice for enterprise software development. C++: A staple in the gaming and systems development industries, C++ offers exceptional performance and memory management. Swift: Apple's preferred language for iOS app development, Swift continues to grow in popularity with its simplicity and reliability. R: As data science and machin...
C program to Find Cartesian Product of Two Sets | C programming
C program to find the Cartesian Product of two sets Cartesian product is a mathematical operation that returns a set (or product set or simply product ) from multiple sets. That is, for sets A and B , the Cartesian product A × B is the set of all ordered pairs ( a , b ) where a ∈ A and b ∈ B . Products can be specified using set-builder notation, e.g. {\displaystyle A\times B=\{\,(a,b)\mid a\in A\ {\mbox{ and }}\ b\in B\,\}.}


Comments
Post a Comment
Subscribe Us and Thanks for visiting blog.